Everyone needs a password manager these days and many people were using LastPass. Unfortunately, LastPass made some pretty horrible mistakes that mean that these people should look for an alternative now. Here’s why.
Please note: The will probably be no episode next week. I need to take care of some stuff that most likely will leave me unable to record a podcast during that week.
 This podcast episode was recorded with a live audience on my Twitch channel. Recordings of these streams get saved to a YouTube playlist so you can watch them on demand at your leisure.
This podcast episode was recorded with a live audience on my Twitch channel. Recordings of these streams get saved to a YouTube playlist so you can watch them on demand at your leisure.
Why You Need to Use a Password Manager
Before we get into what happened at LastPass, I think it’s important to remind everyone that using a password manager is absolutely essential today. It is the only way to safely deal with our modern digital lives and the internet infrastructure we have built to secure them.
That password manager will most likely store data in the cloud, which is the only way to make it convenient (which means its the only way it can be used by people who aren’t completely insane nerds). But that is OK, we have developed ways of doing this safely – the rest of the episode will discuss how not to do it safely, though.
You simply need to think about what you want to achive with your setup and who you are defending against. And what password managers don’t defend against: namely local attacks. And yes, having a paper password notebook can be a totally sensible option, believe it or not.
How LastPass Failed
LastPass is probably the most popular password manager in the world, which is why they are a big target for attacks. They have been breached over a dozen times since 2011 – the product was released in 2008. But the two most serious attacks happened in 2022.
In August, the company advices users of a security incident:
On August 25, 2022, LastPass published a blog post notifying customers that a third party gained unauthorized access to portions of their development environment, source code, and technical information through a single compromised developer account.
The data that was misappropriated in this hack led to a second attack that was publicised in November. Full details of this second, much worse, hack were disclosed by LastPass shortly before Christmas:
In November, LastPass published updates on the security breach and stated that some customer data was accessed by a third party. LastPass assured users that passwords stored with the service were still secure, as encryption and decryption of passwords takes place on the user’s device.
In December, LastPass reported that the actor obtained a backup of customer data and the customer vault data (the password databases) by using some of the information obtained in the August breach. The customer data included customers' names, billing addresses, phone numbers, email addresses, IP addresses and partial credit card numbers. The vault data included, for each breached user, unencrypted website URLs and site names, and encrypted usernames, passwords and form data for those sites. According to the report, the stolen info did not include the user’s master password, which would be required to access the encrypted portions of the vault data (such as usernames and passwords), and which LastPass does not store. The report suggested that, providing a strong master password and many rounds of encryption were applied, it would take millions of years to decrypt the passwords. The report did not reveal when the vault data backup was made, when the vault data was stolen, how many users were affected, which fields in the vault data were encrypted or not, nor if vault metadata was taken (including number of rounds of encryption used on the encrypted portions of the vault).
This raises a security and a privacy issue. Let’s discuss the security issue first.
The Security Issues
→ Since LastPass is not telling us how many password vaults were copied, we must assume that every single one of their users was compromised.
→ Since they are not saying when this backup was made, every single user must assume that this copy of their vault was protected by the least secure master password they ever had on their account.
While the security of the stolen password vaults is technically intact, there are some procedural mistakes LastPass made that very likely present serious issues for their users. They never upgraded the security of the process which is used to encrypt the vault for individual users.
How a password manager works: To encrypt your data (passwords, URLs of login pages, credit card numbers) on your local computer before storing the resulting secured data blob in the cloud, a password manager needs to create an AES key. It cannot store this key safely, so it must be regenerated every time data is encrypted or decrypted based on something the user knows. This is the master password. This master password is turned into an AES key by using a key derivation function.
At LastPass, the general principles of how the encryption key is generated from the master password weren’t kept up to date:
- Some passwords might be encrypted with weaker AES-ECB instead of the generally accepted industry standard AES-CBC (see this explanation of block cipher modes on Wikipedia)
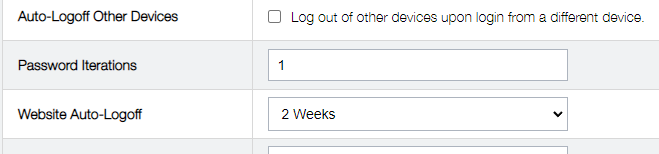
- Some users PBKDF2 iterations are set to very insecure numbers like 500 or 5000, or even 1 (see PBKDF2 on Wikipedia)
- LastPass never seems to have enforced users creating a longer master password than 8 characters
This was my PBKDF2 iterations setting when I checked this week:
Almost all of my passwords were encrypted with AES-ECB as well:
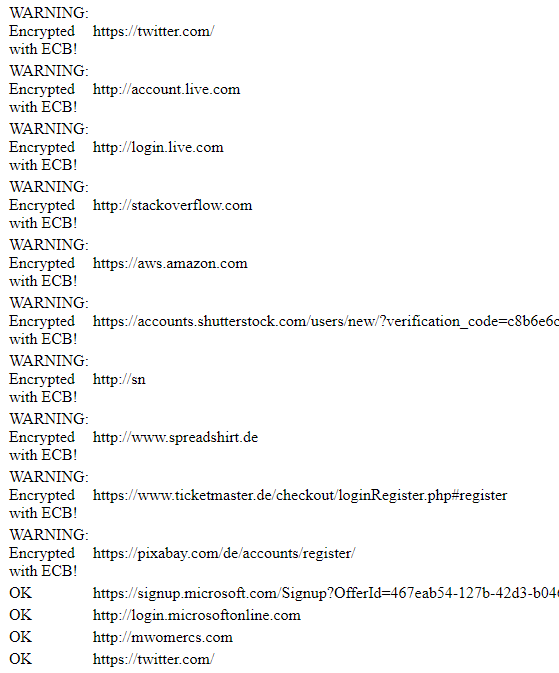
To check this, I used the tool Steve Gibson talked about in Security Now! episode 905 that was developed by one of that show’s listeners.
So it looks like LastPass used sensible security settings back when the software was first developed, but then neglected to update the security of its users' password vaults during the next decade. Which is a problem, because we can now use GPUs to crack passwords.
The result of this is that if you had a master password with insufficient entropy (because it was short and/or easily guessable), you now have to assume that the passwords you stored in your LastPass vault have been compromised.
The Privacy Issues
Aside from the security problems, LastPass also made a pretty big blunder in the way they encrypted (or didn’t) people’s vaults, that presents a significant privacy issue. They didn’t encrypt some metadata that many other password managers routinely encrypt along with passwords, including the URL for the login page belonging to the password.
This means that whoever made off with these LastPass vaults can now build a profile of users, based on what sites they frequented, without even having to decrypt the vaults. This was a known issue with LastPass since at least 2017, and might in itself be as good a reason for this hack as any other. Especially for an intelligence service or other state-sponsored actors.
It is also pretty handy in trying to figure out which vaults you might want to attack.
There is really no excuse for a software that claims having the security and privacy of their users be their number one concern to leave this data unencrypted on their servers. Especially when it would have been trivial to encrypt it along with other data like passwords. Just as it is inexcusable to not update the security of your existing user accounts along with increased security measures for new users.
Password Manager Alternatives
In the wake of all of this horribleness, you should probably switch away from LastPass. There are two alternatives that I have tried in the last few years that I can recommend:
- 1Password is probably the best choice for users who are less technical literate.1
- I personally use BitWarden, which is a bit less polished, but has the additional benefit of being open source.
BitWarden can also be hosted on your own server, if you are into that kind of thing.
Whatever software you use, you should make sure you use a secure master password. The general rule of thumb is: The longer the password, the better. In reality, more entropy is the best defence, but since it’s impossible for most people to remember a combination pseudo-random characters, you can just make the password long and maybe use a few tricks like character substitutions that are unique to how your particular brain works.
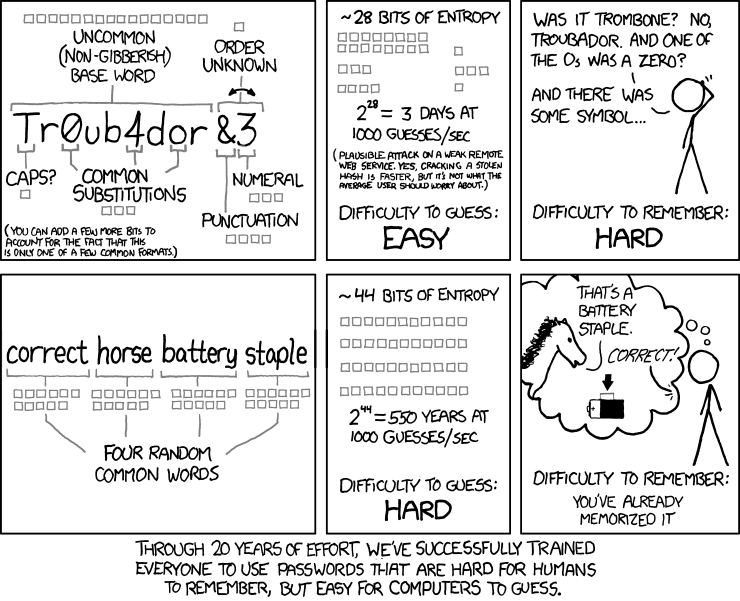
The famous XKCD comic on password strength (source: XKCD/936)
Steve Gibson from the Security Now! podcast maintains some resources on this topic and a helpful password “search space” calculator at his “password haystacks” page.
Producer Feedback
I value your input greatly. If you have any opinions or remarks on the things discussed in this, or previous episodes, or ideas for future ones, please contact me.
In just over two weeks, the third anniversary of this podcast is coming up and several people have written in to ask me if I have something special planned for this episode (especially seeing as I dropped the anniversary episode last year to finish the manuscript for my novel). My current thinking is that I will release an episode that explains my history in journalism and why I now do this show now, since I have been asked about this regularly over the last few years. If you have any specific questions for me regarding this or any other topics you might find interesting for that episode, please let me know.
Credits
This podcast is provided free of charge and free of obligations under the value-for-value model. However, as a freelance journalist volunteering my time to produce this show, I need your support. If you like my work and want to make sure The Private Citizen keeps going, please consider joining my Patreon.
Showrunners
- Sir Galteran
- IndieGameiacs
Executive Producers
- Butterbeans
- Jaroslav Lichtblau
- Rizele
- Sandman616
Supervising Producers
1i11g, avis, Bennett Piater, Dave, ikn, Jackie Plage, Jonathan M. Hethey, krunkle, Michael Mullan-Jensen, Robert Forster
Producers
Andrew Davidson, astralc, Cam, Captain Egghead, David Potter, Dirk Dede, Florian Pigorsch, Joe Poser, Michael Small, Mika, MrAmish, Rick Bragg, RJ Tracey
Associate Producers
Barry Williams, D, Jonathan, Juhan Sonin, Kai Siers, RikyM, Steve Hoos, Vlad
Thanks to Bytemark, who are providing the hosting and bandwidth for this episode’s audio file.
The show’s theme song is Acoustic Routes by Raúl Cabezalí, licensed via Jamendo Music. This episode’s ending song is Final Run by Lupus Nocte, licensed via Epidemic Sound.
-
Full disclosure: I have a free family account from them as part of their journalism initiative. ↩︎